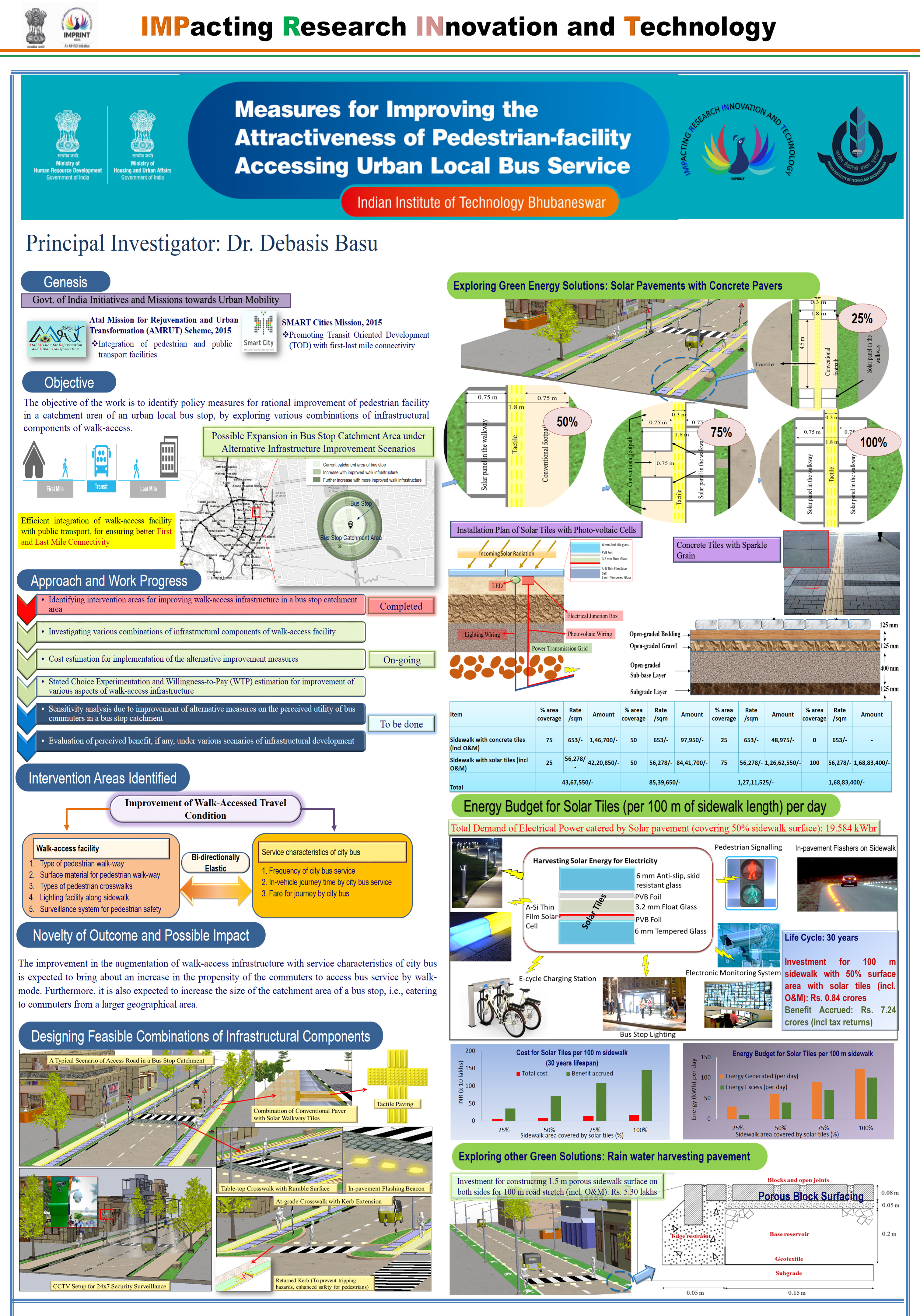
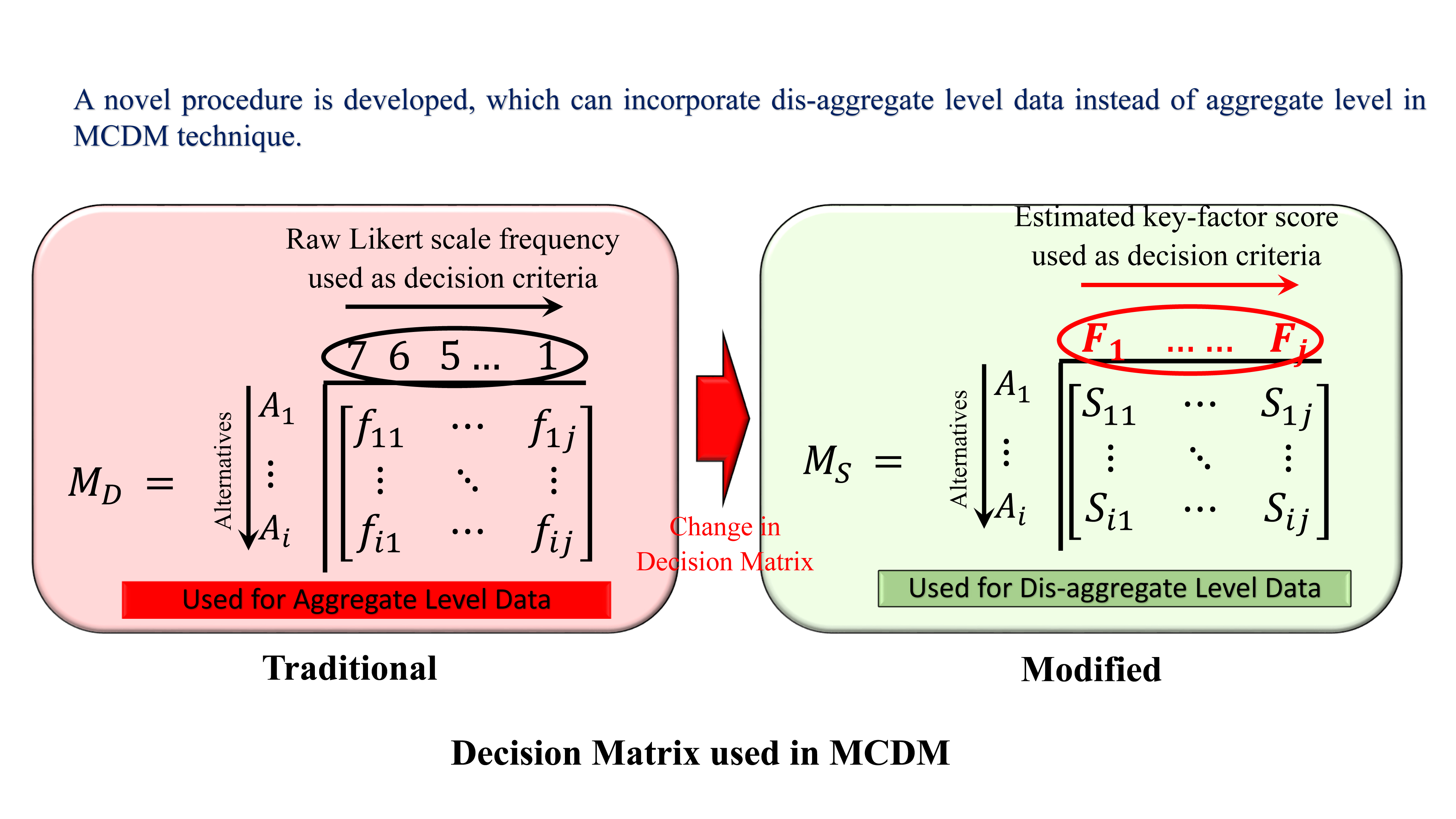
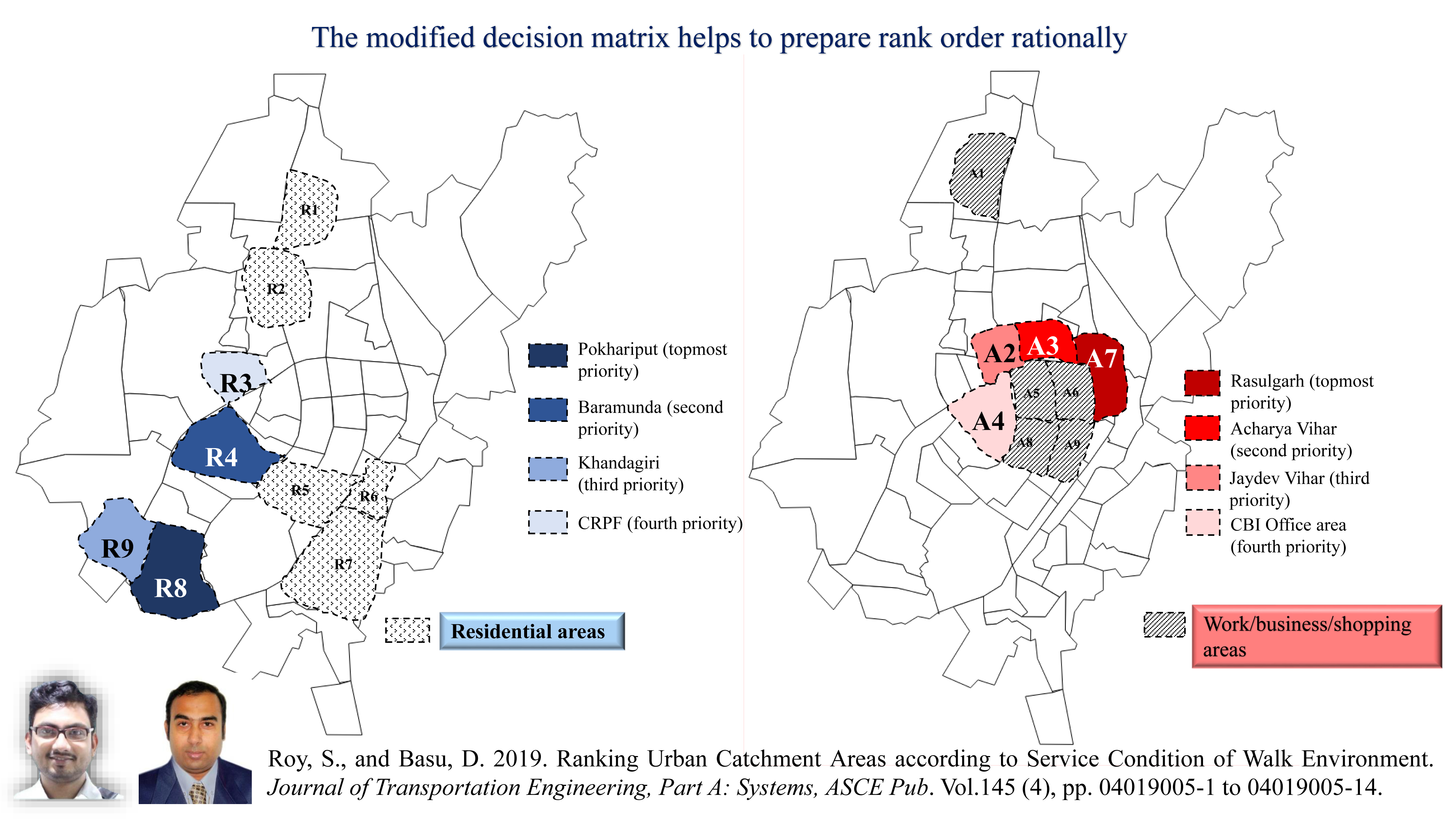
Research Highlights
Greywater treatment and reuse by combined sequencing batch reactor and solar photocatalytic reactor
Description
The aim of the project is to develop a new process for the treatment of greywater by a combined biological and advanced oxidation process. Sequential batch reactor (SBR) and solar photocatalytic reactor (SPCR) was used respectively for the degradation of pollutants by biological method and by advanced oxidation process. The developed technology can be used for the effective reuse of greywater at the community level and multistoried residential buildings to effectively reuse the greywater for gardening and groundwater recharge.
Core Faculty with research focus in this area:

|
Assistant Professor
School of Infrastructure
|
Names of students associated with project along with their affiliations:
Kumari Priyanka, SIF
Names of organizations associated with the project:
IIT Bhubaneswar
Details of publications and patents related to the project
1.Kumari Priyanka, Manaswini Behera, Remya Neelancherry, Evaluation of performance for the treatment of low strength greywater using sequencing batch reactor, 11th International Conference on the Challenges in Environmental Science and Engineering (CESE-2018), 4 to 8 November 2018, Bangkok, Thailand.
Microwave photocatalytic treatment for soft drink beverage industry wastewater
Description
The soft drink industry in India is growing at the rate of 5 to 6% annually. The soft drinks are available in two distinct segments i.e., cola drinks and the non-cola drinks such as soda, clear lime, cloudy lime and drinks with orange and mango flavours. Soft drink industries extract a great portion of groundwater, adding pressure to the water scarcity issues. On the other hand, these industries suffer inadequate handling of their product losses generally considered as wastes. Those products contribute to the wastewater organic load augmentation and cause fastidious environmental impact. The current practices of the soft drink beverage industry wastewater is either time consuming, sensitive to the variations in the wastewater stream and/or produces a concentrated waste stream at the end of treatment process, which has to be handled separately. Therefore, research work was intended to develop a method for rapid and complete treatment of soft drink wastewater.
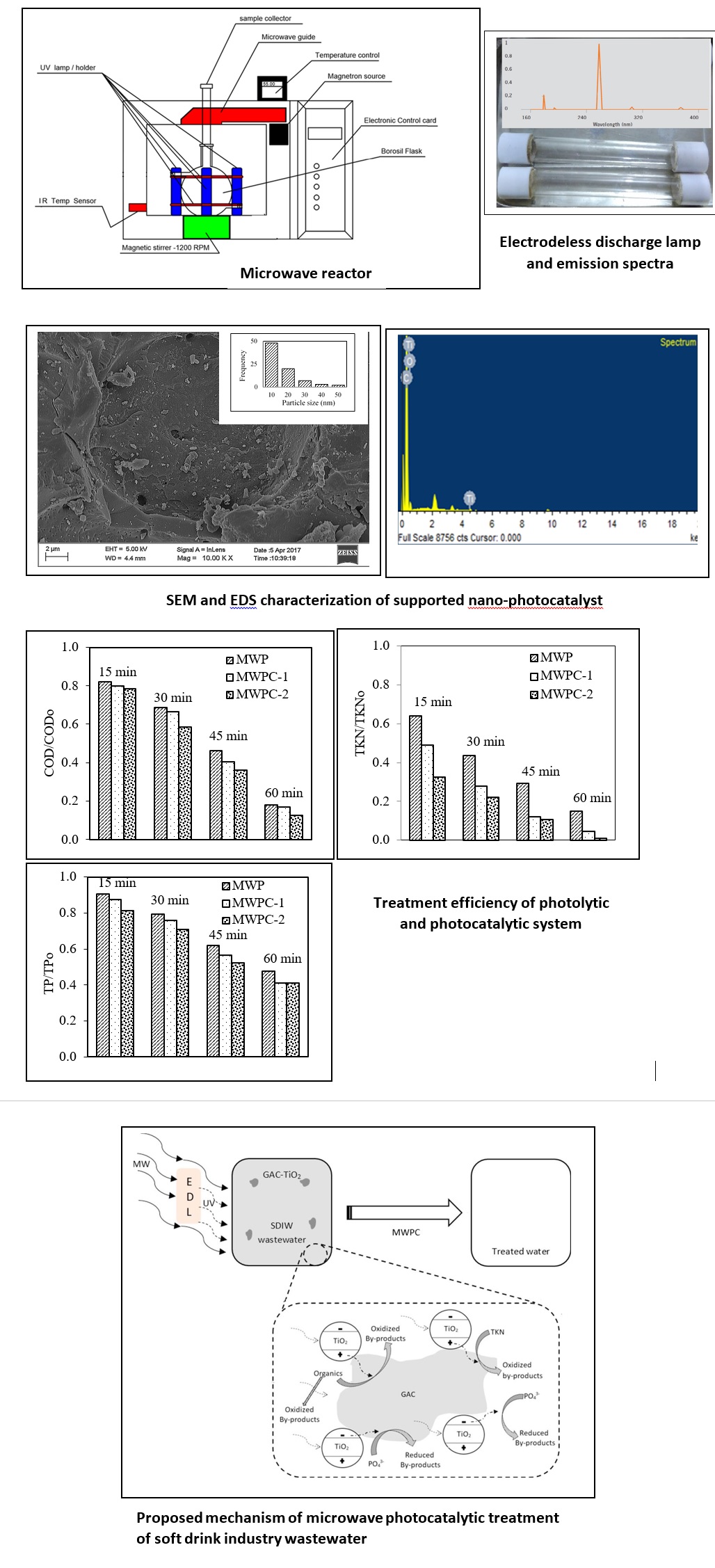
Core Faculty with research focus in this area:

|
Assistant Professor
School of Infrastructure
|
Names of students associated with project along with their affiliations:
Anil Swain, SIF
Names of organizations associated with the project:
IIT Bhubaneswar
Details of publications and patents related to the project
1.Remya N, Swain A, Soft drink industry wastewater treatment in microwave photocatalytic system Exploration of removal efficiency and degradation mechanism, Separation and Purification Technology, Volume 210, 8 February 2019, 600-607
https://www.sciencedirect.com/science/article/pii/S13835866183270472.Anil Swain, Neelancherry Remya, Analysis of photolytic and photocatalytic systems for the microwave coupled treatment of soft drink industry wastewater�, 3rd Green and sustainable chemistry conference, 13 to 16 May 2018, Berlin Germany.
3.Anil Swain, Neelancherry Remya, Microwave Photolytic Treatment of Soft Drink Industry Wastewater�, Recycle 2018, International Conference on Waste Management, 22 to 24 February 2018, Indian Institute of Technology Guwahati India.
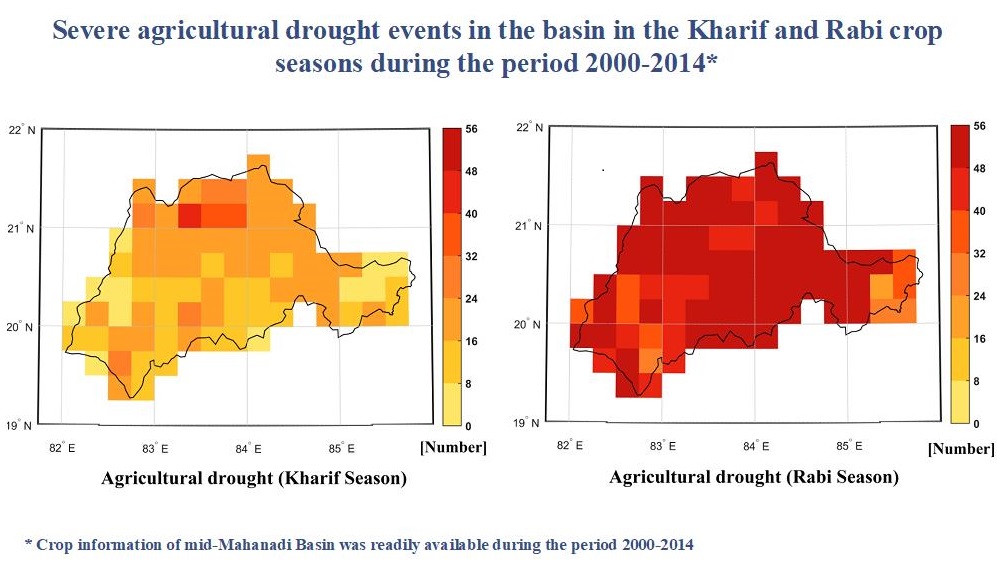
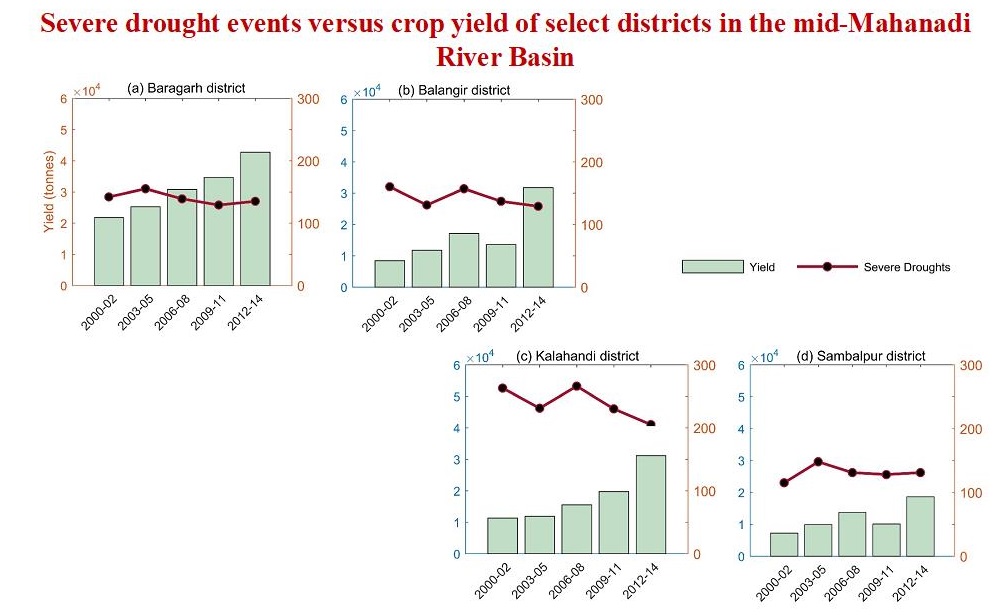
Description
The cropping season is classified into two main seasons in India: kharif and rabi. While the kharif season is from June to October, the rabi is from November to March. Using a crop water stress indicator, severe agricultural droughts over Mid-Mahanadi river basin were extracted for the two seasons over the period 2000-2014 at monthly scale, at 25° grid resolution. The drought stress indicator built on soil type, crop coverage and remotely sensed surface soil moisture data of the region aids in agricultural drought classification and monitoring. The effect of severe and extreme category agricultural drought events in the region on crop yields of four drought-hit districts of the state of Odisha during the period is also demonstrated. The study was presented in the World EWRI Congress held at Sacramento, USA, in May 2017.
Core Faculty with research focus in this area:
|
|
Assistant Professor on Contract
School of Infrastructure
|
Research Domain:
Drought Monitoring
Development of an Integrated Zero Energy Modular System for the Treatment of Rural Domestic Wastewater: Emphasis on Nutrient Removal
In this research project, newly designed natural laminar flow aerofoils are optimized for higher lift to drag ratio which have possible applications in the transport aircrafts. Aerodynamic characteristics of the newly developed aerofoils are obtained using CFD simulations using high accuracy numerical schemes.
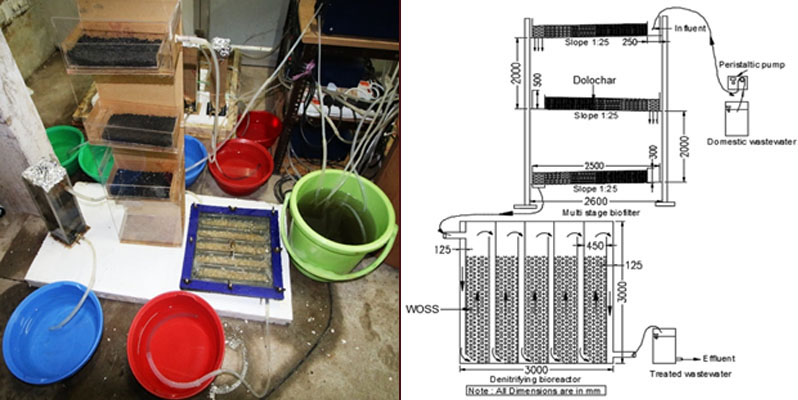
The process flow of a single representative integrated system (b) the schematic diagram of the designed experimental set-up with all the dimensional details.
Description
In a developing country like India, providing reliable and affordable wastewater treatment facilities in rural areas are a huge challenge. With the aim of enhancing the nutrient removal from rural domestic wastewater while reducing the cost of the treatment process, a novel, integrated treatment system consisting of a multistage bio-filter with drop aeration and a post positioned attached growth carbonaceous denitrifying-bioreactor was designed and developed in this work. The bio-filter was packed with 'dolochar', a sponge iron industry waste, as an adsorbent mainly for phosphate removal through physiochemical approach. The Denitrifying bio-reactor was packed with many waste organic solid substances (WOSS) as carbon sources and substrates for biomass attachment, mainly to remove nitrate in the biological denitrification process. The performance of the modular system, treating real domestic wastewater was monitored for a period of about 60 days and the average removal efficiencies during the period were as follows: phosphate, 99.48%; nitrate, 92.44%, ammonia, 96.64%, with mean final effluent concentration of 0.153, 5.5, and 1.06 mg/L, respectively. The multistage bio-filter played an important role in ammonium oxidation and phosphate adsorption. The multilevel drop aeration with increasing oxygenation, and the special media used, consisting of certain oxides were likely beneficial for nitrification and phosphorus removal, respectively, whereas the nitrate was effectively reduced by biological denitrification in the carbonaceous bioreactor. This treatment system would allow multipurpose reuse of the final effluent. Moreover, the saturated dolochar can be used as nutrient suppliers in agricultural practices and the partially degraded carbonaceous substances can be subjected to composting, and subsequently used as an organic fertilizer. Thus, the system displays immense potential for treating domestic wastewater significantly decreasing the concentrations of nutrients and most importantly, facilitating the conversion of the waste materials into usable ones.
Core Faculty with research focus in this area:

|
Assistant Professor
School of Infrastructure
|
 |
Assistant Professor
School of Infrastructure
|
Research Domain:
Environmental Biotechnology
Related Link to published work:
http://pubs.rsc.org/en/content/articlepdf/2016/RA/C6RA08519AMacrophyte assisted vermifilter (MAVF) to treat wastewater
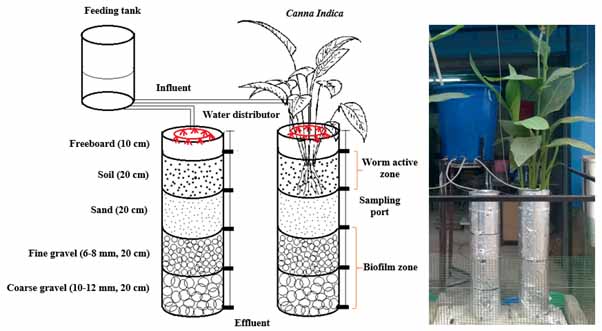
Description
Macrophyte assisted vermifilter (MAVF) is a bio-oxidative process in which detritivore earthworms interact symbiotically with microorganisms and other soil fauna to degrade organic contaminants present in wastewater. Microbes perform biochemical degradation of wastewater solids, while earthworms degrade and homogenize the material through muscular actions of their foregut. Earthworms can exert an influence on soil microorganisms directly or indirectly via comminution, burrowing, casting, grazing and dispersal process. Presence of macrophyte in vermifilter, enhance physical filtration process and organic solids present in wastewater filtered and trapped in the bed for a long time, thereby allowing for better biodegradation of solids. Plant roots distribute effectively on bed and provides natural habitat, which encourages the development of a great diversity of microbial communities. Nutrients in wastewater uptake by the roots and oxygen leakage from root tips create a 1-4 mm oxidation film surrounding the roots, which enhance the aerobic degradation process. Pathogens present in wastewater reduced due to the action of intestinal enzymes (protease, lipase, amylase, cellulase) secreted in the earthworm's body wall and coelomic fluids released from their body cavity (coelom). Root exudates released from the plant also have antimicrobial activity which kills pathogen present in wastewater. Overall, this system requires no skill persons to operate, which is economically affordable and environmentally sustainable.
Core Faculty with research focus in this area:

|
Assistant Professor
School of Infrastructure
|
 |
Assistant Professor
School of Infrastructure
|
Research Domain:
Wastewater treatment
Impact of Climate Change on Design of Offshore Wind Turbine
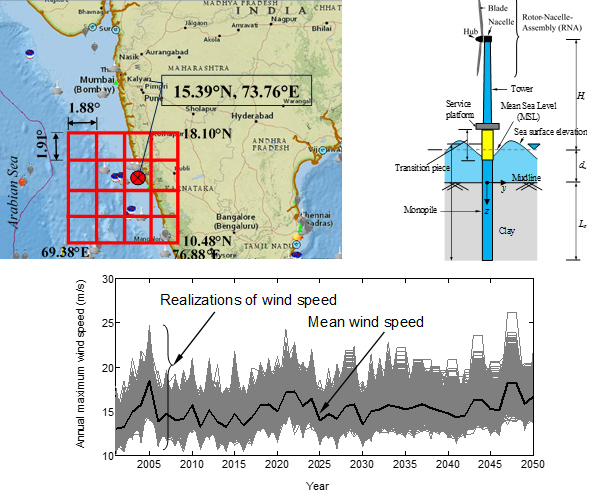
Description
India is planned to develop offshore wind energy in coastal areas. This would include exploiting India's 7,500 km-long coastline for the production of low-carbon energy from offshore wind power. Global warming is expected to change the wind and wave patterns at a significant level, which may lead to condition outside current design criteria of monopile supported offshore wind turbine (OWT). This study examines the impact of climate change on the dynamic behavior and future safety of offshore wind turbine. The time series of future wind speed and wave height at local level is generated using a statistical downscaling model. Wind speed, wave height and wave period data are collected from the buoy deployed by Indian National Centre for Ocean Information Services and the future climate for the next 30 year is simulated considering various greenhouse gas emission scenarios. The changes in design at offshore location along the west coast of India is examined considering serviceability and fatigue limit state criteria. This study shows that changes in design of OWT are required due to increased responses owing to the effect of climate change. Fatigue life is found to be decreased because of climate change. These aspects are important for designing of offshore wind turbine.
Core Faculty with research focus in this area:

|
Associate Professor
School of Infrastructure
|
Research Domain: Offshore wind energy, Sustainability
Related Link to published work:
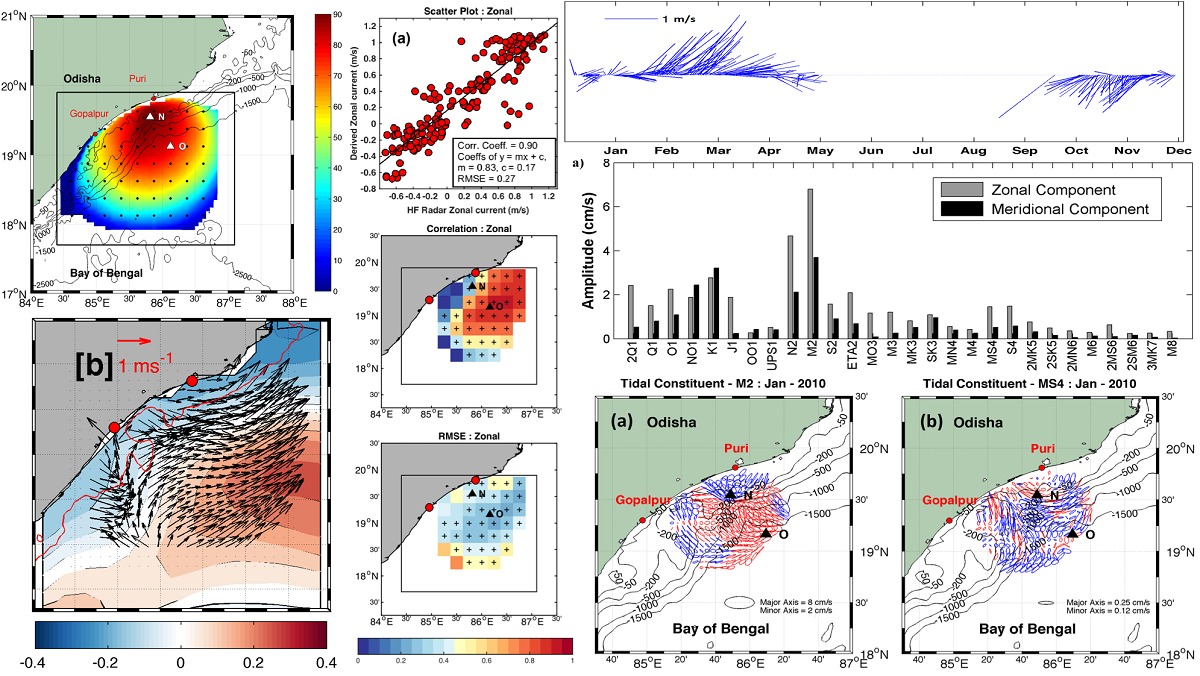
http://www.tandfonline.com/doi/full/10.1080/1064119X.2016.1257671Extraction of high frequency tidal signals from High Frequency Radar Currents in the Bay of Bengal
Description
The surface currents along the north-western BoB are characterized to be northward (southward) alongshore flow during February to April (October to December) with peak magnitude of about 1.8 (1.2) m/s. Validation of the High Frequency Radar (HFR) derived ocean surface currents on daily scale and the high frequency tidal constituents have been carried out in the north-western Bay of Bengal (BoB). Diurnal, semi-diurnal and high frequency tidal constituents (shallow water) have been extracted from systematic harmonic analysis of the currents. Among the semi-diurnal tidal components, M2 dominates over S2 and N2, leading to the simultaneous occurrence of a cycle of high and low tides twice. Significant shallow water constituents M4, MS4 and M3 are identified, which are due to non-linear interaction of tidal currents with bathymetry (Mandal et al., 2018).

Ocean Circulation Modeling Studies for the Indian Ocean
Description
Ocean Circulation Model using Regional Ocean Modeling System (ROMS), a three-dimensional, free-surface, terrain-following model, has been set up for the Indian Ocean to study the intra-seasonal to inter-annual circulation variability (Dey et al., 2017) in this domain. Several sensitivity experiments were carried out to assess the model responses to various air-sea fluxes and the boundary conditions. The model was extensively validated with all observational data. The recent eddy permitting model set up is running with TropFlux (source: INCOIS) forcing and boundary condition from SODA.

1.Indian ESSO - Indian National Centre for Ocean Information Services (INCOIS) (RP082)
2.Science and Engineering Research Board (SERB) (RP086)
3.Ministry of Earth Sciences (MoES) (RP088)
4.Space Application Centre (SAC)- Indian Space Research Organisation (ISRO) (RP139)
Core Faculty with research focus in this area:

|
Assistant Professor
School of Earth, Ocean and Climate Sciences
|
Names of students associated with project along with their affiliations:
2.Mr. Saikat Pramanik, Research Scholar, SEOCS
3.Mr. Abhuijit Shee, Research Scholar, SEOCS
4.Ms. Nibedita Behera, Research Scholar, SEOCS
5.Mr. Dipanjan Dey, M. Tech. Student, Climate Science and Technology, SEOCS
Research Domain:
Physical Oceanography, Ocean Circulation Modeling
Details of publications and patents related to the project:
Dipanjan Dey, Sourav Sil, Sudip Jana, Saikat Pramanik, P.C. Pandey (2017), An assessment of TropFlux and NCEP air-sea fluxes on ROMS simulations over the Bay of Bengal region. Dynamics of Atmospheres and Oceans. Vol. 80, 47-61, https://doi.org/10.1016/j.dynatmoce.2017.09.002
Risk based Security Enforcement in Software Defined Framework
Batakrishna Tripathy, Debi Prasad Das, Swagat Jena, Padmalochan Bera
Research Domain: Network Security, SDN, Risk Analysis
Computer & Security, Elsevier, Vol 78, pp 321-335, 2018
Publication Link: https://www.sciencedirect.com/science/article/pii/S0167404818301913?via%3Dih
Details:
Software Defined Network (SDN) paradigm provides intelligent and efficient management of different network control functions (NF) depending on changes in traffic behaviour, service providers' requirements and application context. However, the logical centralization of controllers' functions opens up several security challenges over the underlying network perimeter and the assets. In this paper, we propose a risk assessment model for pro-active secure flow control and routing of traffic in SDN. The proposed model determines threat value of different SDN entities by analyzing vulnerability and exposure with respect to Common Vulnerability Scoring System (CVSS). The risk of a given traffic is calculated as cumulative threat values of the SDN entities that guides the flow and routing control functions in generating secure flow rules for the forwarding switches. The efficacy of the proposed model is demonstrated through extensive case studies of an�enterprise network.
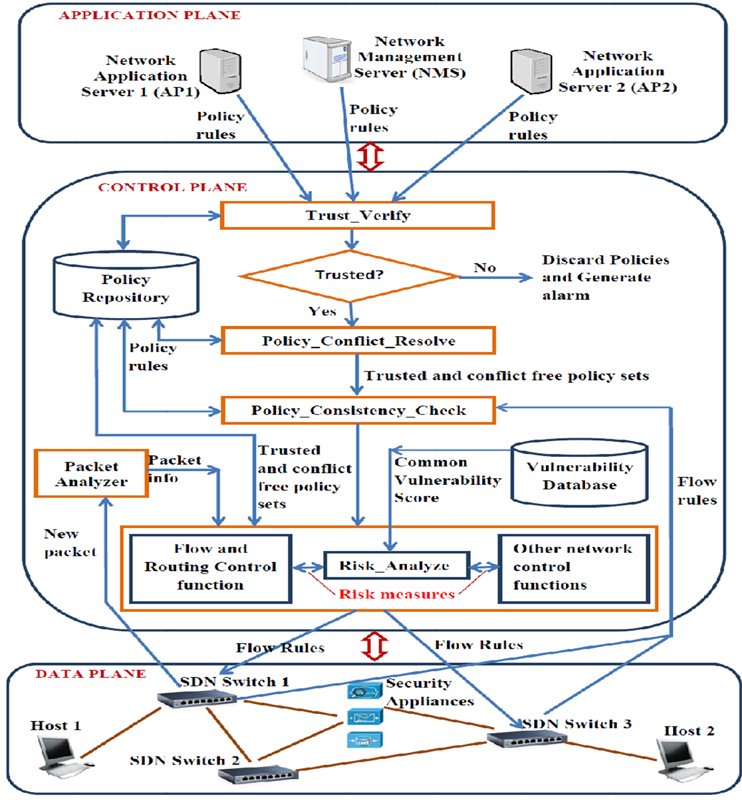
Figure: System Model Risk based of Security Enforcement in SDN
Distributed Multi-authority Attribute-based Encryption using Cellular Automata
Ankit Pradhan, Kamalakanta Sethi, Shrohan Mohapatra, Padmalochan Bera
Research Domain: Cryptography, Data Security
18th International Conference on Cryptology and Network Security, Fozhou, China, 2019
Details:
Cellular automata (CA) has attracted the attention of research communities for its applications in the design of symmetric and public-key cryptosystems. The strength of cellular automata lies in its inherent data parallelism, which can help accelerate access control mechanisms, and its information scrambling capabilities, which can enhance the security of the system. Also, the cryptosystems designed using CA do not involve number-theoretic methodologies that incur large computational overhead like traditional cryptosystems. However, existing CA-based cryptosystems encompass a limited set from the set of all possible transition rules indicating the existence of CA cryptosystems which are possibly unbreakable but have not been explored sufficiently. Thus, they have not yet been considered for applications involving fine-grained access control for heterogeneous access to the data. In this paper, we propose a secure distributed multi-authority attribute-based encryption using CA, which has potential applications in cloud systems. Our cryptosystem adopts the concept of multi-authority attribute-based access control where the encryption and attribute distribution use reversible CA, and policy satisfiability is achieved by Turing-complete CA in a distributed environment. We illustrate the practical usability of our proposed cryptosystem, in terms of efficiency and security, by extensive experimental results.
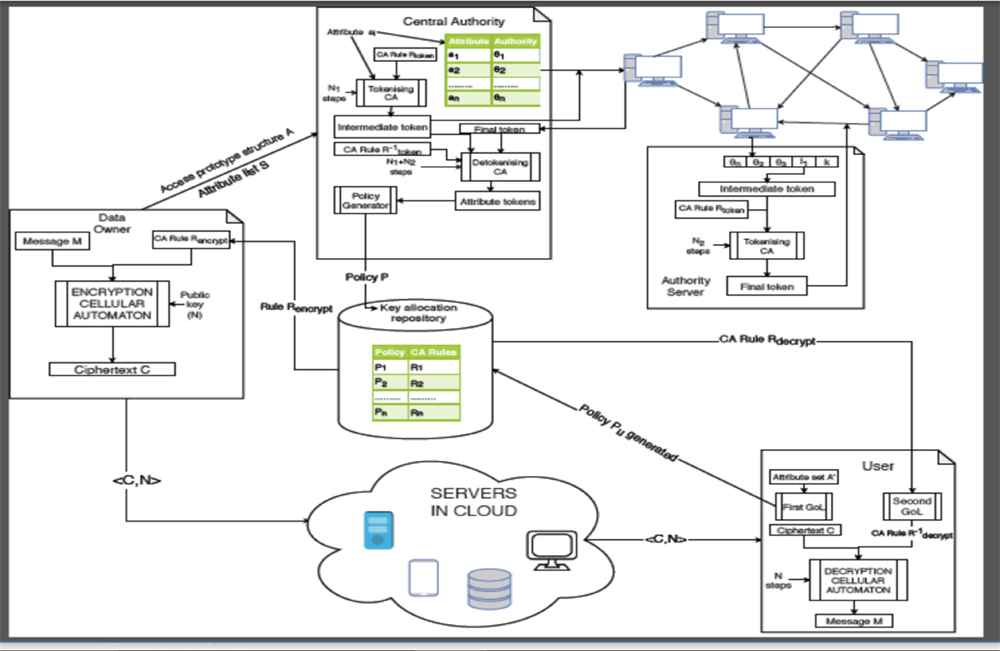
Figure : System Model of Proposed Cryptosystem
A Novel Machine Learning based Malware Detection and Classification Framework
Kamalakanta Sethi, Rahul Kumar, Padmalochan Bera
Research Domain: Malware Detection, Network Security
IEEE Cyber Security, University of Oxford, UK, June 2019
Details:
As time progresses, new and complex malware types are being generated which causes a serious threat to computer systems. Due to this drastic increase in the number of malware samples, the signature-based malware detection techniques cannot provide accurate results. Different studies have demonstrated the proficiency of machine learning for the detection and classification of malware files. Further, the accuracy of these machine learning models can be improved by using feature selection algorithms to select the most essential features and reducing the size of the dataset which leads to lesser computations. In this paper, we have developed a machine learning based malware analysis framework for efficient and accurate malware detection and classification. We used Cuckoo sandbox for dynamic analysis which executes malware in an isolated environment and generates an analysis report based on the system activities during execution. Further, we propose a feature extraction and selection module which extracts features from the report and selects the most important features for ensuring high accuracy at minimum computation cost. Then, we employ different machine learning algorithms for accurate detection and fine-grained classification. Experimental results show that we got high detection and classification accuracy in comparison to the state-of-the-art approaches.
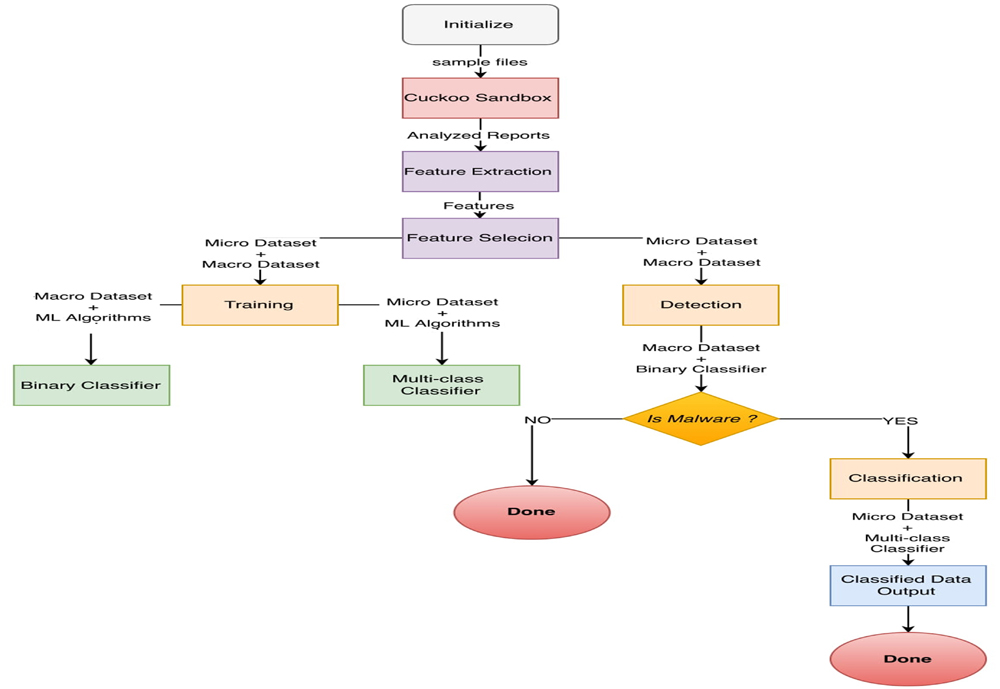
Figure : Operational Flow of Proposed Methodology
An energy-efficient load distribution framework for SDN controllers
Madhukrishna Priyadarsini, Shailesh Kumar, Padmalochan Bera, M.A. Rahman
Research Domain: Software-defined Network (SDN), Network Traffic Managament
Journal of Computing (Springer), DOI
10.1007/s00607-019-00751-2, 2019
Publication link: http://link.springer.com/article/10.1007/s00607-019-00751-2
Details:
Software-defined networking (SDN) has evolved as an effective platform for future Internet due to its capability of configuring the network dynamically with varying requirements. It has been observed that the load and energy requirement of SDN devices increase significantly with the growth of communication networks. Therefore, there is a need for efficient modeling of SDN controller that can balance the load as well as optimize the energy consumption by the devices. In this work, we present an energy-efficient load distribution framework; controller system model for efficient load distribution and routing of traffic that objectively optimize the energy consumption in the network. Our model balances load according to the heterogeneous traffic demands as well as reduces energy consumption by introducing energy-efficient routing algorithm selection procedure. The load balancing scheme is drifted by switch migration technique for multiple controllers simultaneously, whereas the novelty of energy-efficient routing lies on sleep and active mode of network devices. We present interaction between load-balancing scheme and energy-efficient routing towards the network's performance enhancement. The efficacy of our proposed controller system model is justified with extensive simulation results that show approximately 25% reduction of energy consumption and approximately 20% performance increment. Our proposed model is applicable to real-life network environment satisfying the standards of green communication.
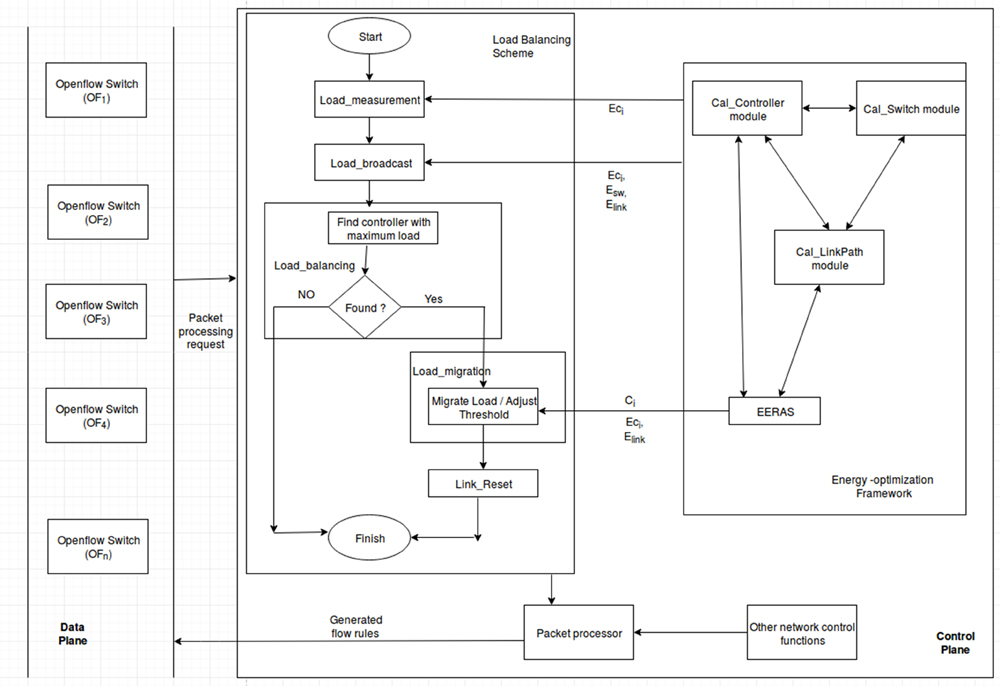
Figure : Functional architecture of proposed controller system model (CSM)
A Secure Virtual Controller for Traffic Management in SDN
Madhukrishna Priyadarsini, Padmalochan Bera
Research Domain: Software-defined Network (SDN), Network Function Virtualization
IEEE Letters of the Computer Society, vol.2 (3), 2019
Publication link: https://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=8788591
Details:
There is a need for developing an efficient, robust, and secure execution platform for Software-defined networking (SDN) concerning the dynamic network service offerings. In this work, we present a secure virtual controller (SVC) architecture that satisfies the benchmark characteristics and provides robustness, fine-grained modularity, strong isolation. Our proposed architecture supports network function virtualization, which is responsible for executing different network functions on various traffic flows. We designed two new network functions that provide vigorous security enforcement and energy-efficient load distribution in SDN. The security function is realized using signaling game theory, and the load distribution is accomplished using a heuristic-based approach. Finally, the performance of our proposed architecture is evaluated and compared with the state-of-art research works and the commercially available controller Floodlight.
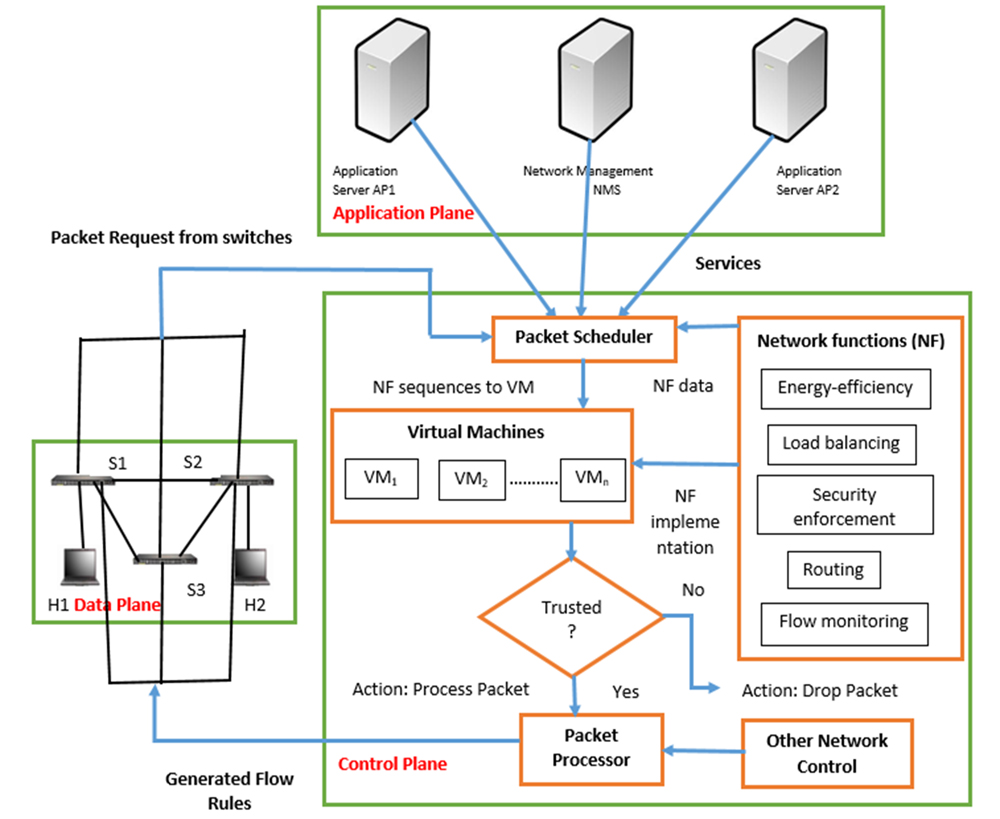
Figure : Proposed Secure Virtual Controller (SVC) Architecture
Characterization of dense crowd gatherings at socio-cultural events through visual surveillance
Abstract
Large gatherings at socio-cultural events often cause traffic congestion in cities, or even they lead to untoward incidents such as stampede or accidents. However, if the crowd dynamics can be understood or predicted, precautionary measures can be taken by the administrative authority. Crowd dynamics in terms of energy, entropy, order parameter, or density helps us to understand the crowd behavior and characterize crowd videos in terms of randomness and orderliness. In a similar context, the analysis of crowd flows also helps in understanding crowd behavior. We have developed model to understand crowd behaviors, detect abnormal crowd behavior, and can also help in predicting abnormal events in large gatherings such as Sri Jagannath Ratha Yatra, Bali Jatra, Kumbh Mela, etc.
Publication: S Behera, D P Dogra, and P P Roy. "Characterization of dense crowd using Gibbs entropy." Proceedings of 2nd International Conference on Computer Vision & Image Processing. Springer, Singapore, 2018.

Segmentation of crowd flows in videos of Sri Jagannath Ratha Yatra event of 2016.

Depiction of how energy and entropy of the gathering varies over time for the video of Sri Jagannath Ratha Yatra event of 2016.
Configuration Compliance checking, Security Policy verification and Threat Diagnosis for ECN
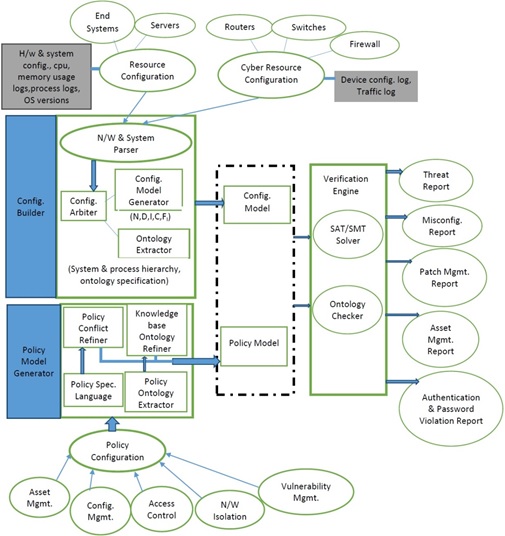
NetAssure Architecture
Description
In enterprise networks (ECN), the correct implementations of security policies are becoming increasingly difficult due to complex and heterogeneous organizational requirements involving a large number of computing and cyber devices. These policies may span from resource health and configuration management to dynamic access control and protection against emerging vulnerabilities and related attacks. The complexity of the problem is compounded due to dynamic change in configurations and network topologies, inter-dependencies between device level configurations, and distributed nature of implementing policies in the networks. In addition, dependencies between network services may introduce hidden access channels which in turn may expose the organizational resources to the attackers. Recent studies show that 60-80% of security vulnerabilities are due to network policy misconfigurations. The manual analysis and enforcement of the security policies can be overwhelming and potentially inaccurate due to high potential of human errors. Therefore, there is significant need of developing tools for formally assessing the compliance between the distributed security implementation and the organizational policies.
The main objective of this project is to develop an automated compliance checking, security verification and diagnosis tool for Enterprise Computing and Network Infrastructure (called NetAssure) to identify various functional violations and security threats. The tool provides the following security analytic capabilities:
- Asset_Checker: compliance checking of the enterprise resources (hardware and software) based on device level system parameters, drivers, application software and OS versions; related vulnerabilties, risks and patches as specified under enterprise policies/requirements. The key enabler for this module is formal ontology extraction supported verification.
- Config_verifier: verification of the device level configurations and the distributed network access control implementations with respect to the organizational policies, various security standards and known attack scenarios. Predicate logic based constraint solver is used for modeling and verification engine. It also generates remediation plans based on the verification traces.
- Auth_diagoniser: diagnosis of conflicts between heterogeneous role-based authorization and resource access policies and its implementations. This will also cover detection of password violations and generation of run time alerts.
- Network Isolation Enabler: automatic enforcement of separation between network devices or group of network devices (zones) driven by device functionality, exposure (to/from internet), potential vulnerabilities (running software) of the connected hosts and heterogeneous access policies. Configuration based ontology extraction and analysis will be used for enforcement of network isolation.
- Disposal Manger: automatic checking of the methodology and devices used for disposal of data and resources.
Collaborator: SAG, DRDO, New Delhi
Research/Experimental Platform:
- XML based Formal Policy Specification Language
- Yices SMT Logic based Verification Engine
- Epic small scale live Network for validation
Core Faculty with research focus in this area:
Prof. Ehab Al-Shaer, Prof. Sajal Das, Prof. Patrick McDaniel, Dr. Mathew Ceiser, Dr. Mohammed Ashiqur Rahaman, Elisa Bertino, Dr. Manoranjan Satpathy, Dr. Padmalochan Bera

Research Domain: Network Security, Formal Verification.
Related Link to published work: http://dblp.uni-trier.de/pers/hd/b/Bera:Padmalochan
Homomorphic Encryption for Secure Data Storage in Cloud
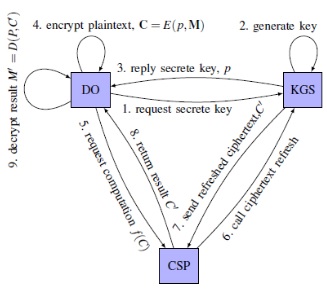
Proposed cryptosystem for Homomorphic encryption
Description
Due to the digitization of data in large scale and varying requirements of the organizations to serve different
stakeholders, there is a need to compute, store and analyze large amount of data often in remote servers efficiently. Cloud computing provides a platform to compute, store and share data remotely for heterogeneous entities and provides services to them according to their demand. One of the major challenges in cloud computing platform is to ensure security and privacy of the data. The major limitation of applying existing cryptosystem such as AES, 3-DES, etc. is the need of decryption of ciphertext for outsourced computations that may violate data security. Homomorphic encryption is a solution which allows performing computations directly on cipher text without decrypting of the ciphertext. In this work, we develop efficient model to implement different algorithms related to benchmark computations on ciphertext. In addition, we work on parallel implementation of these algorithms. We also design cryptosystems with function level encryption, integration of Role Based Access Control (RBAC) with parallel Homomorphic encryption, and attribute based encryption to harden the security perimeter over remotely stored data.
Research/Experimental Platform:
- Multi-threaded Implementation platform for Homomorphic Cryptosystem
- Interface for Role based Access Control Integration with Homomorphic Cryptosystem
- Map -Reduce Framework for Distributed Implementation of cryptosystem
Core Faculty with research focus in this area:
Prof. Debdeep Mukhopadhya, C. Pandu Rangan, Dr. Bimal Roy, Prof. Sajal Das, Prof. Indranil Sengupta, Dr. Padmalochan Bera

Research Domain: Cryptography, Cloud Security
Design of Adaptive Routing Protocol for Mobile Ad hoc Networks

Framework for Designing Adaptive Trust Model
and Routing Protocol
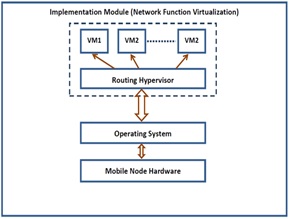
Implementation Module for the Adaptive Trust Model and Routing Protocol
Description
Mobile Ad hoc Network (MANET) has become popular as a key communication technology in many tactical and critical environments, such as military defence networks, disastrous and rescue operations, etc. The recent research on MANET focuses on developing security enforcement mechanisms integrated with routing protocols based on various trust models. In our work, we presented the limitations of the existing trust models in MANET on their applicability with varying contextual requirements and resource constraints with a simulation based comparative study with respect to their performance, and security enforcing features. With this comparative study, an adaptive multi-level trust model and routing protocol for MANET is proposed that supports heterogeneous applications with varying requirements and contexts. Our future work focuses on implementation of the proposed routing protocol for MANET in Software Defined Networking (SDN) platform to integrate and serve heterogeneous applications on a single SDN backbone network.
Research/Experimental Platform:
1. NS3 based Network Protocol Simulation Platform
2. Yices SMT logic based verification engine for protocol verification
3. Texas Instrument Emulation kits for custom protocol design and testing.
Collaborator: Anurag Lab, DRDO, Hyderabad.
Core Faculty with research focus in this area:
Prof. Soumya Kanti Ghosh, Prof. Sudip Misra, Prof. Sajal K Das, Dr. Mohammad Ashiqur Rahman, Dr. Ehab Al-Shaer, Prof. Sukumar Nandi, Dr. Padmalochan Bera

Related Link to published work: http://dblp2.unitrier.de/pers/hd/t/Tripathy:Bata_Krishna
Design and Performance Analysis of SDN Controllers
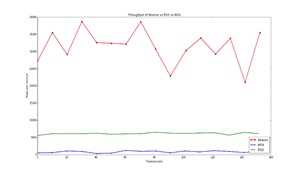
Throughput Comparison of NOX, POX, Beacon Controller
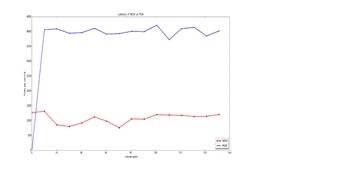
Latency Comparison of NOX, POX Controller
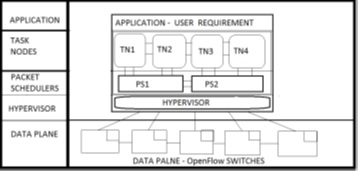
Proposed Architecture for SDN Control Platform
Description
Software Defined Network (SDN) provides a platformto the users and network administrators to efficiently design,build, and manage networks by separating the control plane and data plane. SDN allows to program the control plane and configure the underlying infrastructure based on the applications, network services on demand. However, it introduces degradation of scalability and performance for real time traffic. ThUS, it is important to analyse the limitations and performance of SDN controllers for implementation and deployment in live network environments with applications. This work focuses on performance analysis of SDN controllers supported by simulations. We evaluate number of network virtualization technologies, models and tools to assess the performance of SDN controllers. This study aimed at designing architectural blueprint and control algorithms for efficient SDN controllers with network function virtualization using in-house tools.
Core Faculty with research focus in this area:
Prof. Ehab Al-Shaer, Prof. Mohammad Ashiqur Rahman, Dr. Padmalochan Bera, Dr. David Erickson, Dr. Seungwon Shin, Dr.Wenfeng Xia

Research Domain: Software Defined Network (SDN)
Reconfigurable Optical Magnetometer for Static and Dynamic Fields
Reconfigurable Optical Magnetometer for active detection of static and dynamic magnetic fields utilizing field modulated cavity interferometry technique is demonstrated. It enables the detection of strength and direction of the static field and facilitates dynamic magnetic field detection over a wide frequency range. The large reconfigurability, dynamic operation frequency and portability of the demonstrated magnetometer ascertain practical applications in a broad range of technologies including cardiovascular health monitoring, underground mineral exploration, and marine surveillance.
For details see (Advanced Optical Materials 9 (3), 2001574 (2021))
Faculty member:

|
Associate Professor
|
Research Domain: Optical Instrumentation
Dr. Ashis Biswas's research group from School of Basic Sciences has recently published a manuscript entitled “The impact of different mutations at arginine141 on the structure, subunit exchange dynamics and chaperone activity of Hsp16.3” in Proteins: Structure, Function and Bioinformatics journal (from Wiley publishers). This particular study identified an important amino acid residue (arginine141/R141) in C-terminal extension of Mycobacterium tuberculosis Hsp16.3 which efficiently controls its structure and chaperone function. Furthermore, the results presented in this article laid a good foundation for developing a better second generation vaccine candidate against tuberculosis.

Dr. Biswas is happy to announce that the cover image based on this article has recently been accepted for the Featured Cover of this journal (Vol. 88; Issue 6).
Iteration of Translated tangent
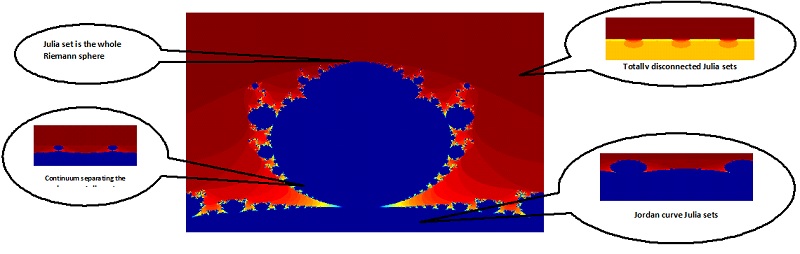
Description
Iteration of a meromorphic function with a single essential singularity is very rich as a dynamical system. We consider the map T_λ: z → λ + tan z on the complex plane. The set of points whose forward orbit is stable under initial (small) perturbation is called the Fatou set and its complement is known as the Julia set of the function . The Julia set of T_λ is found to be either totally disconnected or connected. A necessary and sufficient condition for totally disconnected Julia set is proved. When the Julia set is connected, it is seen that the Fatou set can consist of additional components, which can be completely invariant, a Siegel disk, a two periodic attracting domain or parabolic domain. Further, a necessary and sufficient condition is provided for the Julia set to be a Jordan curve passing through infinity. It is proved that the set of parameters corresponding to Jordan curve Julia sets is connected, shown blue in the base of the picture, whereas the set of those corresponding to totally disconnected Julia sets is disconnected, shown red in the picture.
Faculty member:

|
Assistant Professor
|
Research Domain: Complex dynamics
Related Link to published work :
- 1. Tarakanta Nayak and Jian-Hua Zheng, Omitted values and dynamics of meromorphic functions, Journal of London Mathematical Society, (2) 83 (2011), 1, 121-136
- 2. Tarun Kumar Chakra and Tarakanta Nayak, Iteration of translated tangent .
https://arxiv.org/abs/1211.1816
https://www.researchgate.net/publication/305212944_Iteration_of_the_translated_tangent
Measurement of CP asymmetry in the D0 to K0S K0S decay at Belle
Although Big Bang should have created equal amounts of matter and antimatter in the early universe, what we see around us is made almost entirely of matter. This leads to the inference that something must have happened to cause this matter anti-matter asymmetry. According to Russian physicist, Andrei Sakharov, Charge-conjugation-Parity (CP) violation could be one of the reasons for the same.
We measure the amount of CP asymmetry seen in the decays of a particle called D-zero (D0) meson into final states of two neutral mesons, called K-short (K0S). This analysis was performed by Ms. Nibedita Dash, research scholar, School of Basic Sciences (SBS) and Dr. Seema Bahinipati, Assistant Professor, SBS in association with Dr. Vishal Bharadwaj, Inspire Faculty, IISER Mohali and Prof. Karim Trabelsi, Associate Professor, KEK, High Energy Accelerator Research Organization, Japan, using large data sample collected by the Belle Collaboration, KEK, Tsukuba, Japan using state-of-the-art analysis techniques.
Nibedita presented her work in the 38th International Conference on High Energy Physics (ICHEP) held in Chicago in August, 2016 and garnered quite an attention of particle physics theorists and experimentalists with her precision measurement. This is the first research output obtained by the Experimental High Energy Physics Group of IIT Bhubaneswar.
We report a measurement of the time-integrated CP asymmetry in the neutral charm meson decay D0 to K0S K0S (the use of charge-conjugate modes is implied) using 921 fb-1 data collected at and near the Upsilon(4S) and Upsilon(5S) resonances with the Belle detector at the KEKB asymmetric-energy e+-e- collider. The observed asymmetry is (-0.02 +/- 1.53 +/- 0.17)%,
where the first uncertainty is statistical and the second is systematic. The CP asymmetry measurement is consistent with the Standard Model expectations and improves the uncertainty with respect to the recent measurement of this quantity by the LHCb collaboration by about a factor of four. Furthermore, it
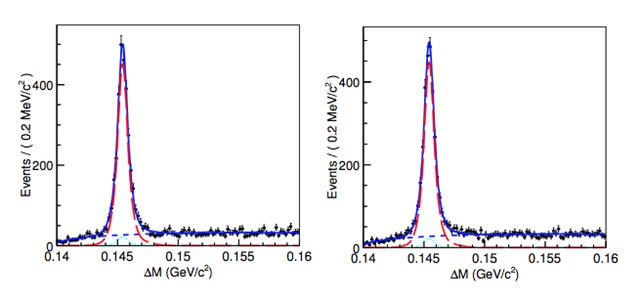
starts to probe the region of interest.
The figure shows the distributions for the mass difference between D* and D0 D* decays to D0 pi. Left (right) plot is for D*+ (D*-). Points with error bars are the data, the solid curve shows the result of the fit, long-dashed (red) is for the signal, dashed (blue) is for the total background and dotted (cyan) is for the peaking background.
Key words: Big Bang, CP asymmetry, Belle Collaboration, Charm meson
Core research group:
Nibedita Dash
Seema Bahinipati
Vishal Bhardwaj
Karim Trabelsi

Research Domain: Experimental High Energy Physics
Related Link to published work:
A. Abdesselam et al., arXiv:1609.06393[hep-ex], Belle Collaboration
How to approach Carnot Efficiency at Finite Power ?
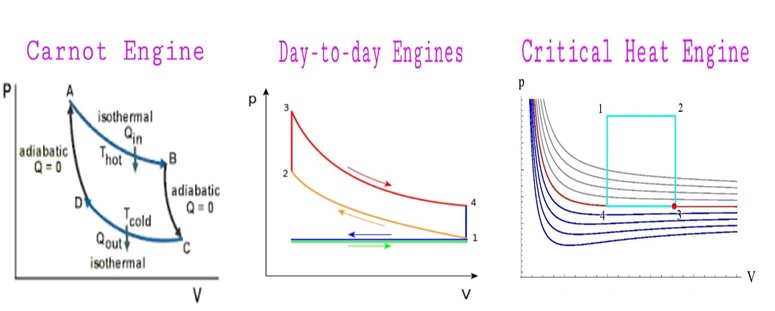
According to the second law of thermodynamics no heat engine can have an efficiency larger than Carnot’s efficiency. The latter can be achieved by the Carnot engine, which however ideally operates in infinite time, hence delivers null power. Increasing the power output of a heat engine has a corresponding cost in terms of reduced efficiency. Vigorous research efforts are being carried out in Science and Engineering, whether it is possible to devise a heat engine that outputs finite power at Carnot efficiency. Having the working substance near criticality (a second order phase transition point of the Van der Waals fluid) is an approach to the problem, exploiting either fluctuations, or a diverging heat capacity to argue for the maintenance of finite power [1]. A working example of this feature was constructed in [1,2] in the context of holographic heat engines where the black hole in question is the working substance [3]. |
 |
Faculty member:
|
|
Assistant Professor
|
Research Domain: Black Holes and Efficiency of Heat Engines
Related Link to published work :
M. Campisi and R. Fazio, Nature Communications, https://www.nature.com/articles/ncomms11895;
C. V. Johnson, https://arxiv.org/abs/1703.06119;
C. Bhamidipati, P. K. Yerra, Phys. Lett. B(2017), http://dx.doi.org/10.1016/j.physletb.2017.07.052
C. Bhamidipati, P. K. Yerra, European Physical Journal C (2017): https://arxiv.org/abs/1606.03223, http://dx.doi.org/10.1140/epjc/s10052-017-5076-2